To achieve HIPAA compliance, healthcare organizations must implement safeguards to protect patient privacy and secure protected health information (PHI). This includes conducting regular risk assessments to identify vulnerabilities, establishing comprehensive policies and procedures, training employees on HIPAA regulations, and ensuring that physical and electronic access to PHI is restricted. Maintaining regular data backups is crucial for protecting patient information and ensuring data recovery in case of a breach or system failure.

HIPAA
Ensure HIPAA compliance with our comprehensive HIPAA checklist. Protect patient data and navigate regulatory requirements seamlessly. Download now!
HIPAA Template
Commonly asked questions
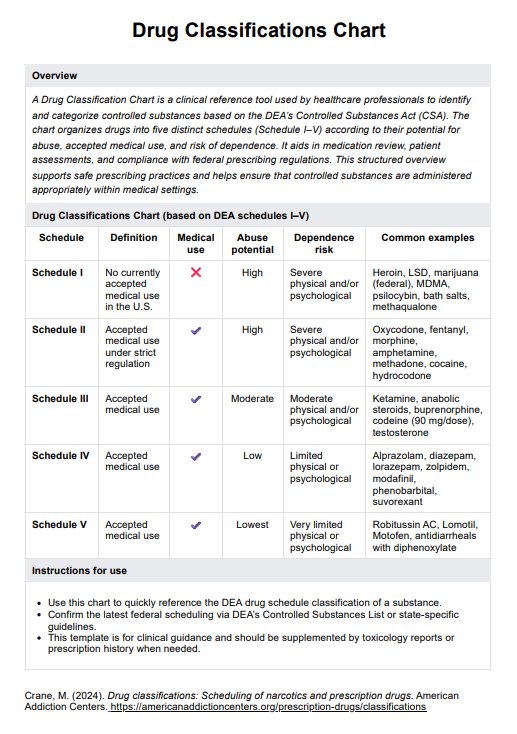
The three important rules for HIPAA compliance are the Privacy Rule, the Security Rule, and the Breach Notification Rule. The Privacy Rule establishes national standards for the protection of PHI. The Security Rule mandates safeguards to protect electronic protected health information (ePHI) through physical, technical, and administrative safeguards. The Breach Notification Rule requires covered entities to notify affected individuals and the OCR in case of a breach of unsecured PHI.
HIPAA compliance documentation refers to the records and policies that organizations must maintain to demonstrate adherence to HIPAA regulations. Key documentation includes policies and procedures, risk assessments, employee training logs, business associate agreements, and records of incidents involving protected health information (PHI).
EHR and practice management software
Get started for free
*No credit card required
Free
$0/usd
Unlimited clients
Telehealth
1GB of storage
Client portal text
Automated billing and online payments